The Custom Row-Level Security plugin applies custom data security for users by querying a remote service.
You can use the Custom Row-Level Security plugin if you have dynamic data security that changes frequently (every few minutes).
On every data query sent to the Sisense server, the Sisense server first sends an HTTP/HTTPS request to a security endpoint to get the updated data security for the logged-in user. The security rules are applied to the query so that the query is processed with the new data security rules.
Important Note: The security endpoint should be implemented by the client and should return the data security rules in the expected format.
Use Case:
A company has a real-time product with complex data security rules. The security rules are saved in a database and are changed often, based on new data that comes in.
Since the company already maintains complex data security rules on their system, they would like to avoid maintaining it twice – once in their database and once in Sisense. In addition, since their data security is changed so often, they want to be assured that the Sisense security rules are always up-to-date.
Using Custom Row Level Security, they can use their existing security database, and make sure the security rules are always up-to-date.
Installing the Custom Row Level Security Plugin
Installing the Server-Side Plugin
- Download the plugin.
- Enable the server-side plugin feature:
- Open the Configuration Manager from your browser: Linux | Windows
- Click the Sisense logo five times to display the full list of services configurations.
- On the API-Gateway tab, enable serverSidePlugins.enabled.
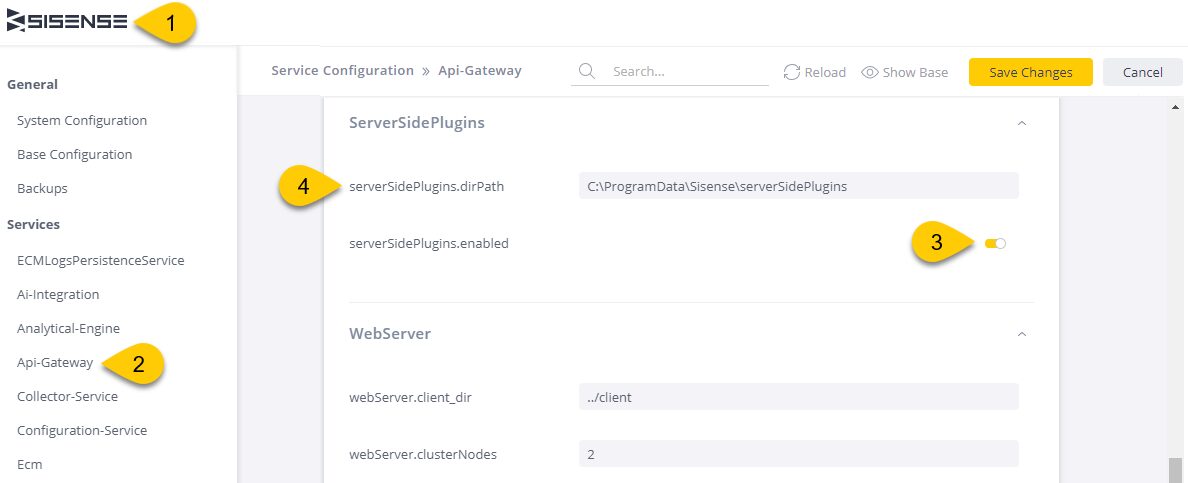
- Place the “serverSidePlugin” folder content in the path specified under the API-Gateway serverSidePlugins.dirPath setting in the Configuration Manager.
- Configure the Custom Row Level Security, as described below.
- Restart Sisense services/ pods:
- Linux: Restart the apigateway pod
- Windows: Restart the Sisense services by clicking “Restart Services” in the Configuration Manager page.
Configuring Custom Row Level Security
The configuration file is located in:
[server side plugin location]/Jaql/addDataSecurityLib/config.json
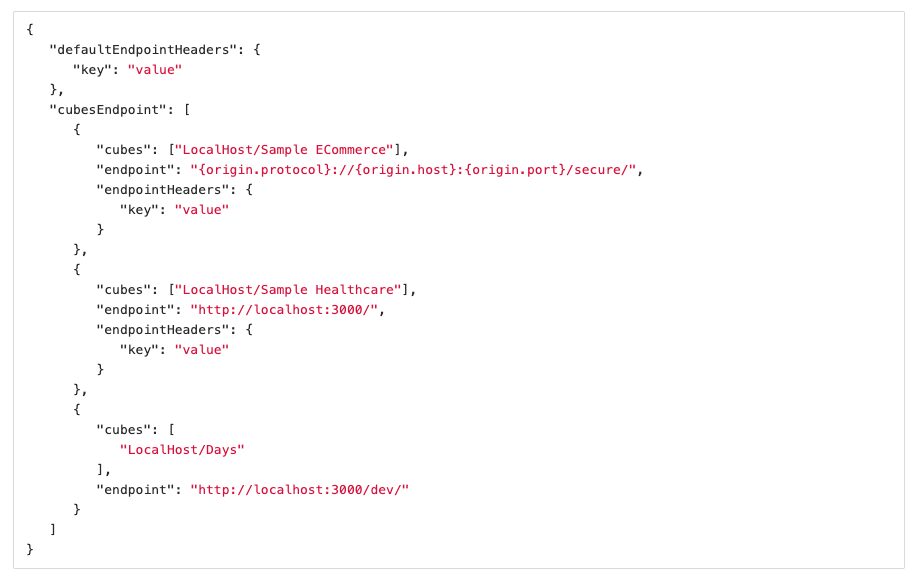
The Configuration Object Keys:
- defaultEndpoint:
String. Url or template url for Data Security Service. The template has the following format: {origin.protocol}://{origin.host}:{origin.port}/{tenant}/secure/.
- Protocol and/or port can be changed for some custom predefined value. For example: http://{origin.host}:3000/secure/
- {tenant} – if provided in the template, will be replace with the current user’s tenant name
- secure – it is a static route for the Data Secure Service and can be any.
If this option is set, security will apply for all cubes. Even a cube has no setup in the cubesEndpoint.
- passEntireRequestBody Boolean. If set to true, interceptors will send the whole body and request headers to the data security endpoint.
- defaultEndpointHeaders Object. Key-value pairs of the default headers that are added to the data security request for the default endpoint.
- cubesEndpoint Array. Contains the Data Security endpoints and headers that the given cubes will get the Data Security rules from. This array is used to decide which Data Security endpoint is triggered for the given JAQL query.
Data Security configuration object keys:
- cubes: Array of full cube name: [address/cube title] (mandatory).
- endpoint: String (mandatory). The data security endpoint for the cube.
- headers: Object (optional). Key-value pairs of the headers that are added to the data security endpoint that is listed above.
Note: The configured security endpoints should be implemented by the client.
Creating a Data Security Rules Service
The Custom Row Level security checks for each query of the data source. Based on the configuration, it sends a query to the configured Data Security Rules endpoint.
The request is sent with some URL parameters:
- user – The user email
- role – User role name
- cube – The full ElastiCube name
- groups – User group IDs
In addition, if specified, some headers are added to the query.
The endpoint returns an object with three keys:
- rules: Array of data security rules, as described below
- includeAll: Boolean (optional). When set to true, the user can see all of the ElastiCube data.
- excludeAll: Boolean (optional). When set to true, the user cannot access the ElastiCube data.
Note: If includeAll or excludeAll are specified, the rules are not taken into account.
The rules array contains objects that describe the data security for a user, group, or role:
- dim: String (optional). The data security dimension
- members: Array of the members that the user should see (optional). When specified the members of the dimension must be set
Return value example:
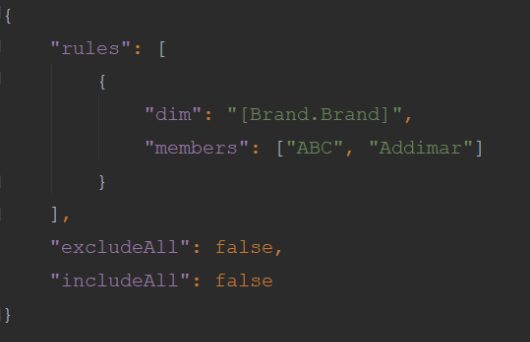
Notes:
- In case a user/role/group has more than one data security rule for an ElastiCube, the priority is:
- Exclude all
- Include all
- Members – union between all members settings
- After every change made to the server-side plugin configuration file, restart the Sisense.Gateway service
- After every system upgrade, run the installation.bat file with Administrator rights
- The data security fields are validated against the ElastiCube. If there is even one field that does not exist in the ElastiCube, the user will not be able to see the ElastiCubedata
- If the user/role/group does not have data security applied to an ElastiCube, the user will not see any data
- If an ElastiCube does not have an endpoint configured in the server side plugin configuration plugin, the ElastiCube will use the Sisense default data security
- ElastiCubesets are supported
This is a premium Sisense add-on. For pricing details please get in touch with
your CSM
Version 1.3.3 – April 8, 2025
- Bugfix: add-on fails to process result in case “Embedded Domain White List” app configuration is not empty
Version 1.3.0 –March 14, 2024
- Added support for multi-tenancy
Version 1.2.4 – July 19, 2023
- Bugfix: Pivot throws an error in case a user should not see any data due to the applied security rule.
Version 1.2.1 – Feb. 3, 2023
- Group names are now passed url-encoded to the endpoint
Version 1.2.0 – Dec. 22, 2022
- Added support for passing user group names instead of group IDs
Version 1.1.1 – July 21, 2022
- Added support for v2 Excel export engine
- Added support for the latest Sisense versions (Windows + Linux)
Version 1.1.0 – Mar. 11, 2022
- Added support for L2022.3
Version 1.1.0 – Feb. 10, 2022
- Added support for L2022.2
- Installation steps have been changed to support installation with scripts
Version 1.0.12 – Jan. 20, 2022
- Added support for L2022.1
Version 1.0.12 – Dec. 09, 2021
- Added support for L2021.12.0
Version 1.0.12 – Nov. 01, 2021
- Added support for L2021.11.0
Version 1.0.12 – Oct. 06, 2021
- Added support for W2021.9.0
Version 1.0.11 – Sept. 27, 2021
- Added support for L2021.10.0
Version 1.0.11 – Sept. 03, 2021
- Added support for L2021.9.0
Version 1.0.11 – Aug. 17, 2021
- Added support for L2021.8.0
Version 1.0.10 – July 20, 2021
- Added support for W2021.6
Version 1.0.10 – June 07, 2021
- Added support for L2021.3.1, L2021.3.2
Version 1.0.10 – April 30, 2021
- Added support for Live models
Version 1.0.9 – March 17, 2021
- Support for L2021.1.4 was added
- Added new option in the solution configuration: forwardCustomHeaders
- Fixed issue with missing data on the PDF / Image
Version 1.0.7 – Feb 26, 2021
- Support for Linux versions L8.2.6 and L2021.1.3 was added
Version 1.0.6 – Feb 11, 2021
- The option to define a default security service endpoint was added (defaultEndpoints)
- Protocol and/or port can be set as a predefined value when using URL parameters
- A route can be added to the security service endpoint
- Sending the entire request body to the security service is now supported (passEntireRequestBody mode)
Version 1.0.5 – Feb 04, 2021
- Support for Windows 8.2.3 was added
- An option to configure a dynamic security service endpoint based on the JAQL request origin was added
Version 1.0.4 – Oct. 26 2020
- Support for Linux L8.2.4 was added
Version 1.0.2 – Sept. 07 2020


